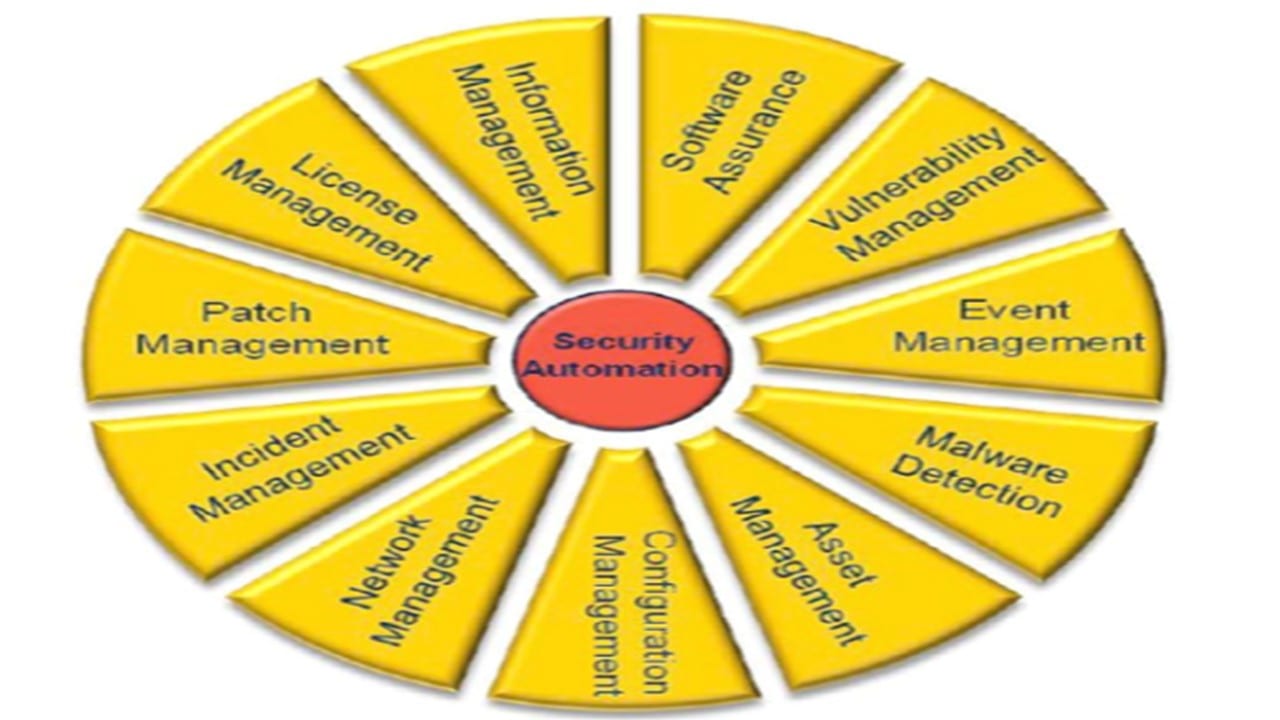
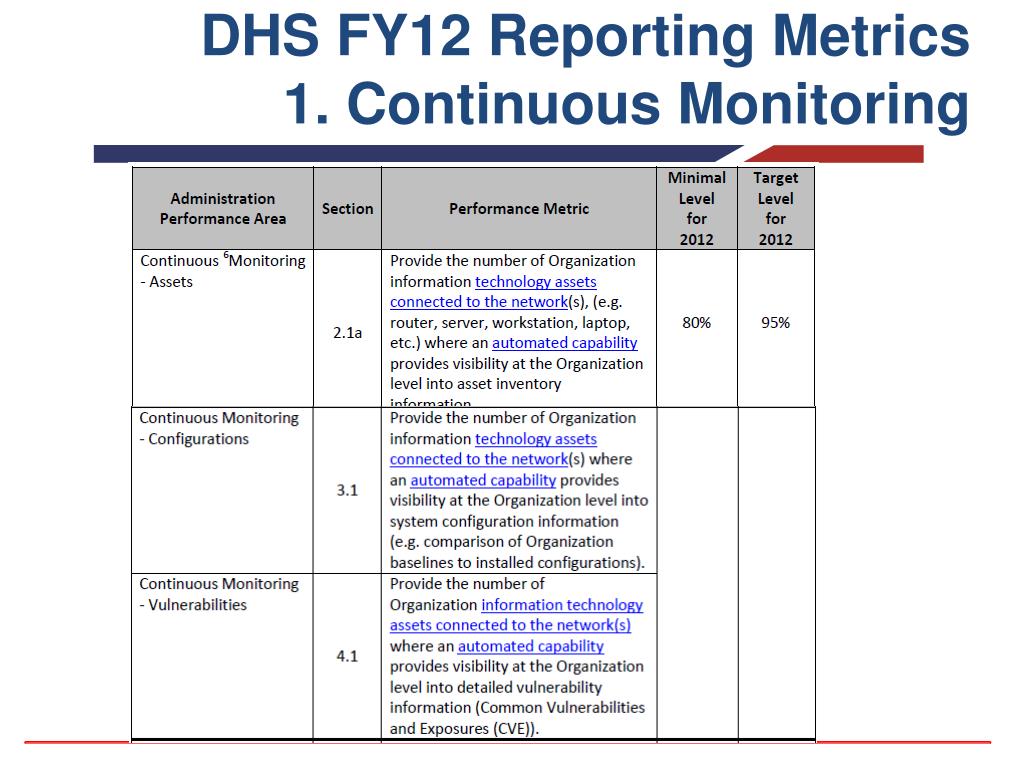
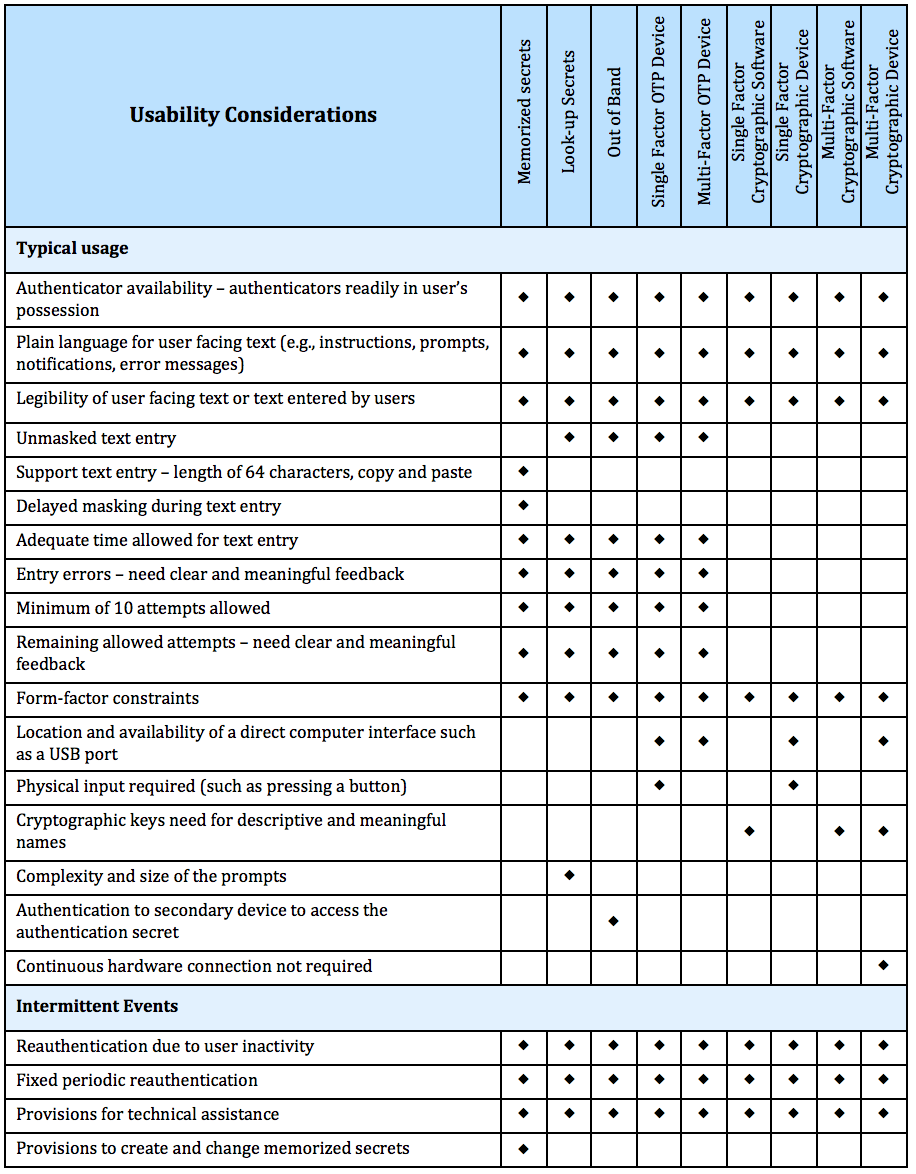
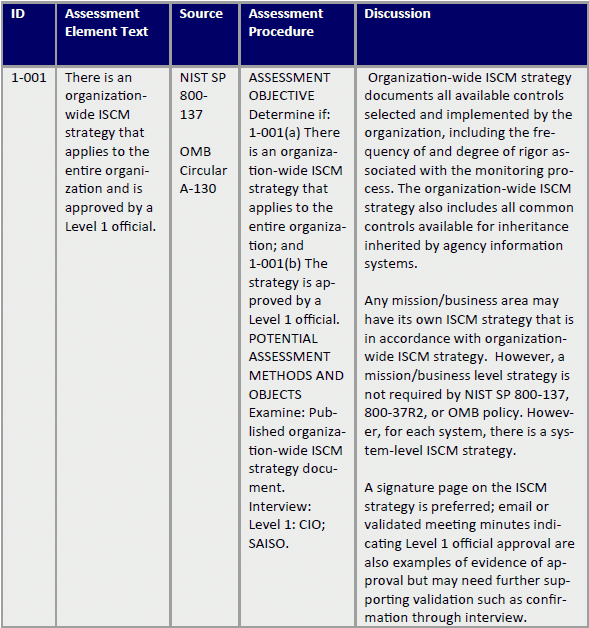
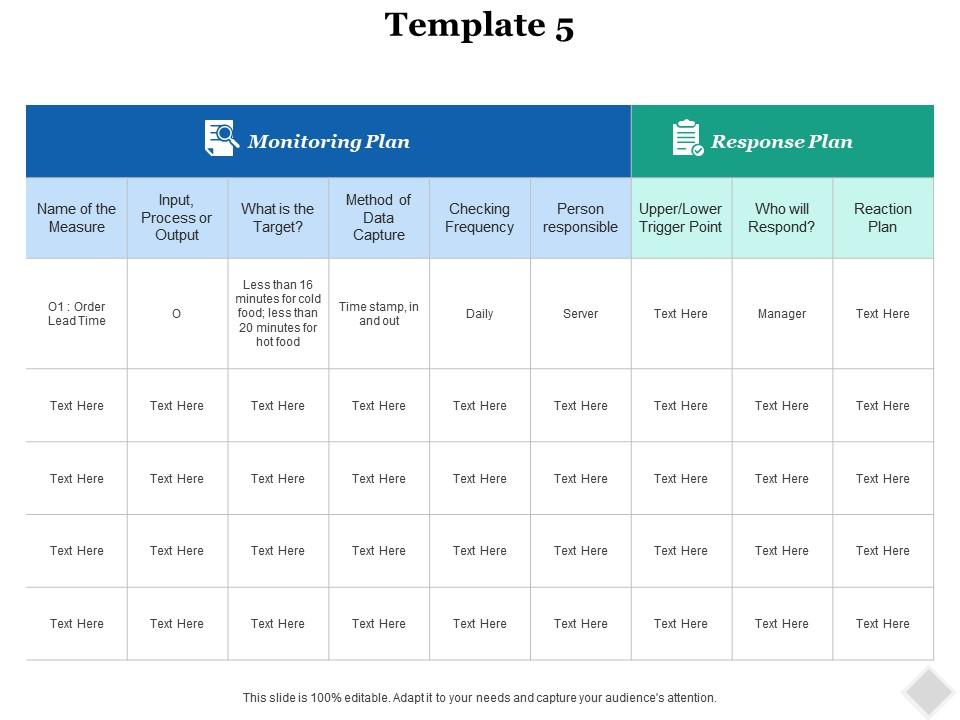
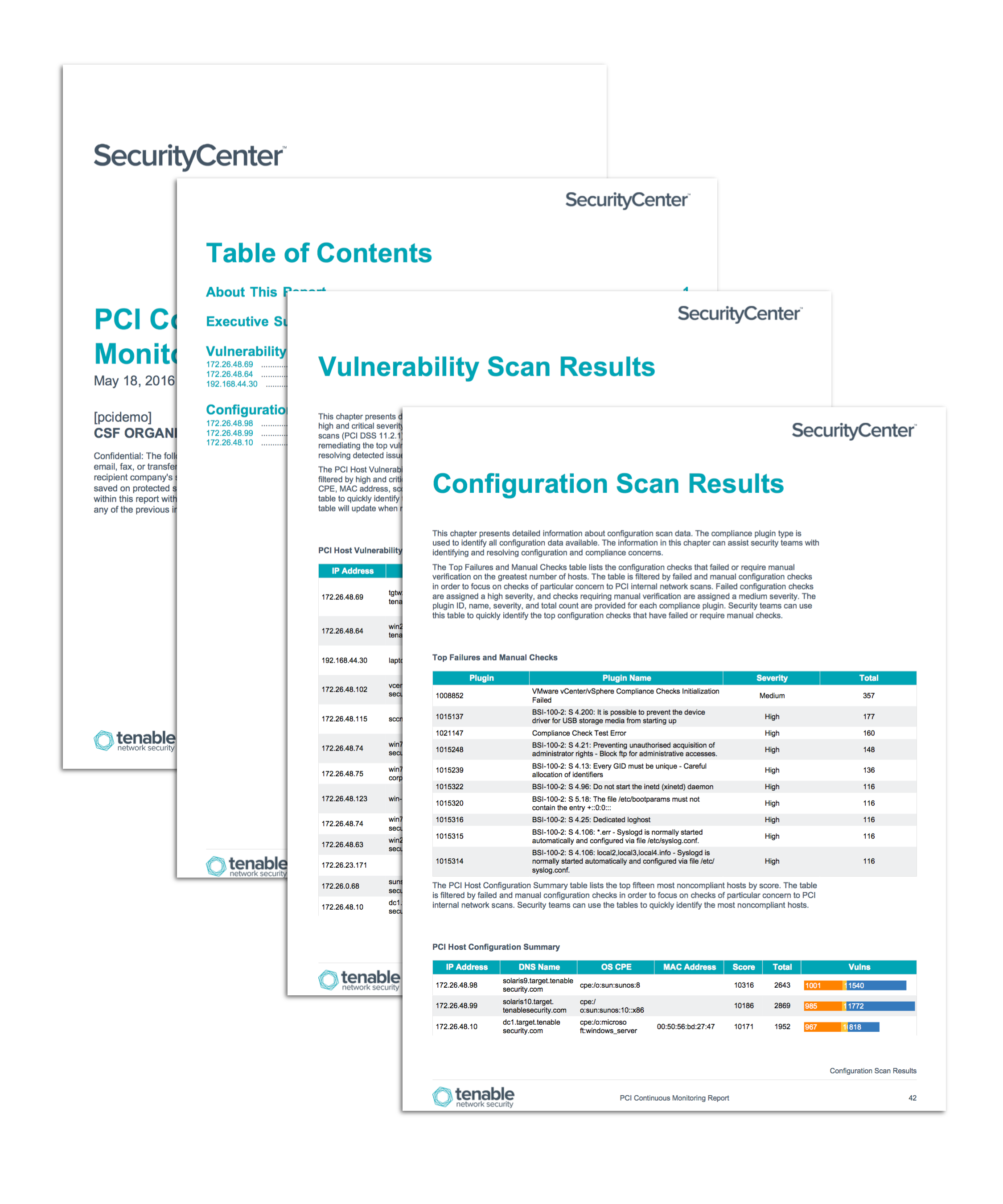
Continuous Monitoring Plan Template - This template summarizes what continuous monitoring (conmon) deliverables must be submitted to the cloud service offering (cso). The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the. Information security continuous monitoring (iscm) is defined as maintaining ongoing awareness of information security, vulnerabilities, and threats.
Information security continuous monitoring (iscm) is defined as maintaining ongoing awareness of information security, vulnerabilities, and threats. This template summarizes what continuous monitoring (conmon) deliverables must be submitted to the cloud service offering (cso). The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the.
Information security continuous monitoring (iscm) is defined as maintaining ongoing awareness of information security, vulnerabilities, and threats. The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the. This template summarizes what continuous monitoring (conmon) deliverables must be submitted to the cloud service offering (cso).
Nist Continuous Monitoring Plan Template
Information security continuous monitoring (iscm) is defined as maintaining ongoing awareness of information security, vulnerabilities, and threats. This template summarizes what continuous monitoring (conmon) deliverables must be submitted to the cloud service offering (cso). The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the.
TEMPLATE Continuous Monitoring Plan (ConMon) ⋆ The Cyber Sentinel
This template summarizes what continuous monitoring (conmon) deliverables must be submitted to the cloud service offering (cso). Information security continuous monitoring (iscm) is defined as maintaining ongoing awareness of information security, vulnerabilities, and threats. The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the.
Continuous Monitoring Plan Template
This template summarizes what continuous monitoring (conmon) deliverables must be submitted to the cloud service offering (cso). Information security continuous monitoring (iscm) is defined as maintaining ongoing awareness of information security, vulnerabilities, and threats. The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the.
Rmf Continuous Monitoring Plan Template
Information security continuous monitoring (iscm) is defined as maintaining ongoing awareness of information security, vulnerabilities, and threats. This template summarizes what continuous monitoring (conmon) deliverables must be submitted to the cloud service offering (cso). The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the.
Nist Continuous Monitoring Plan Template
Information security continuous monitoring (iscm) is defined as maintaining ongoing awareness of information security, vulnerabilities, and threats. This template summarizes what continuous monitoring (conmon) deliverables must be submitted to the cloud service offering (cso). The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the.
Continuous Monitoring Plan Template prntbl.concejomunicipaldechinu.gov.co
This template summarizes what continuous monitoring (conmon) deliverables must be submitted to the cloud service offering (cso). Information security continuous monitoring (iscm) is defined as maintaining ongoing awareness of information security, vulnerabilities, and threats. The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the.
Nist Continuous Monitoring Plan Template
The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the. This template summarizes what continuous monitoring (conmon) deliverables must be submitted to the cloud service offering (cso). Information security continuous monitoring (iscm) is defined as maintaining ongoing awareness of information security, vulnerabilities, and threats.
Rmf Continuous Monitoring Plan Template
This template summarizes what continuous monitoring (conmon) deliverables must be submitted to the cloud service offering (cso). Information security continuous monitoring (iscm) is defined as maintaining ongoing awareness of information security, vulnerabilities, and threats. The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the.
Continuous Monitoring Plan Template
Information security continuous monitoring (iscm) is defined as maintaining ongoing awareness of information security, vulnerabilities, and threats. This template summarizes what continuous monitoring (conmon) deliverables must be submitted to the cloud service offering (cso). The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the.
Continuous Monitoring Plan Template
Information security continuous monitoring (iscm) is defined as maintaining ongoing awareness of information security, vulnerabilities, and threats. This template summarizes what continuous monitoring (conmon) deliverables must be submitted to the cloud service offering (cso). The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the.
This Template Summarizes What Continuous Monitoring (Conmon) Deliverables Must Be Submitted To The Cloud Service Offering (Cso).
The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the. Information security continuous monitoring (iscm) is defined as maintaining ongoing awareness of information security, vulnerabilities, and threats.